I often see Doxxing suspects use Google Docs while collaborating against a victim. They add details as they find them, such as online accounts, email addresses, telephone numbers, and home addresses. These documents can display some valuable information behind the scenes. Let's conduct an example.
I located a Google doc which claims to offer a free PDF version of my OSINT book at the following link (potential spyware warning!):
https://docs.google.com/spreadsheets/d/1KXksB1vj7fXPNS4OYL0idQne3HXVnamtUP1h0ut3xwk
The page source code does not include any owner details, but the Google API does. The easiest way to query this information is through a Python application called xeuledoc available at:
https://github.com/Malfrats/xeuledoc
Installation within your OSINT VM created during the tutorials in my book Open Source Intelligence Techniques, 8th Edition, is quite easy. Enter the following within Terminal.
sudo -H python3 -m pip install xeuledoc
Execute the program by entering "xeuledoc" followed by your target Google Doc. My example was the following:
xeuledoc https://docs.google.com/spreadsheets/d/1KXksB1vj7fXPNS4OYL0idQne3HXVnamtUP1h0ut3xwk
The result identified the creation date, modification date, owner name, owner email address, and owner Google ID. A redacted copy follows.
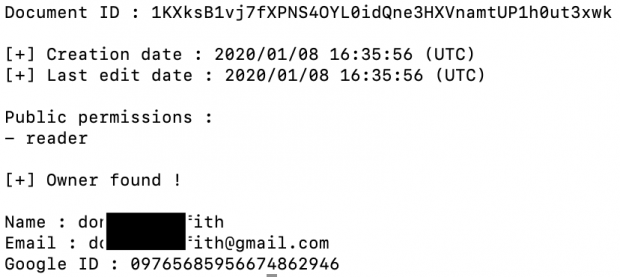
I now know who created and uploaded the document. I can update xeuledoc at any time with the following command, which could be added to your custom update script:
sudo -H python3 -m pip install xeuledoc -U
I have updated the Linux steps and automatic Linux installation script on my website to include this program. You can access this information through the URL/User/Password included with your book. This is quite possibly my favorite new OSINT tool to emerge since publication.