This is the second post of a three-part series about the new ways in which breach data can be beneficial for both offense and defense. Part one can be found HERE.
I am absolutely fascinated by stealer log data. While I have always prioritized breach data as a vital part of our investigations, stealer log data presents a whole new world. First, let's revisit the basics.
Stealer logs are created once a malicious virus has been installed to a computer (typically Windows). The victim may be tricked into installing a program after visiting a malicious website, or the virus could be included within an unauthorized application, such as pirated software. The virus sniffs through the computer to identify, extract, and collect any valuable data. These "logs" are then transferred from the host machine and distributed within shady online locations.
The most common stealer logs we find are labeled as Raccoon Stealer, Redline Stealer, and Vidar Stealer. Criminal marketplaces trade this data as a commodity. They use the stolen data to unlawfully access online accounts, steal cryptocurrency, make unauthorized purchases, and wreak havoc on innocent people's digital lives. Our systems ingest over one million logs every day which are being shared online.
Let's take a look at some real data. In the following example, I extracted a random log which was generated by the Redline stealer and uploaded to a criminal marketplace. I redacted much of the content. First, let's understand the file structure. The following is a tree of a single log file for one victim.
└── US[xx4909xC4Ex3C4x008x57AxD60BBCAF6] [2022-06-19T08_49_35]
├── -----000.txt
├── 00000000000.jpg
├── Autofills
│ ├── Google_[Chrome]_Default.txt
│ └── Microsoft_[Edge]_Default.txt
├── Cookies
│ ├── Google_[Chrome]_Default Network.txt
│ └──Microsoft_[Edge]_Default Network.txt
├── DomainDetects.txt
├── ImportantAutofills.txt
├── InstalledBrowsers.txt
├── InstalledSoftware.txt
├── Passwords.txt
├── Screenshot.jpg
└── UserInformation.txt
Now, let's walk though each folder and file.
└── US[xx4909xC4Ex3C4x008x57AxD60BBCAF6] [2022-06-19T08_49_35]
This top folder presents a two-letter abbreviation of the country of the victim (United States) followed by a unique Hardware Identifier (HWID) and the date and time of capture. The HWID is a security measure used by Microsoft upon the activation of Windows. This unique HWID is generated when the operating system is first installed. This will be vital in a moment. The date and time allows us to know the likely accuracy of the data.
├── -----000.txt
This is an information file about the thief. It often includes generic contact information, pricing for stolen data, and online communities associated with the product.
├── 00000000000.jpg
This is the logo of the Redline product.
├── Autofills
│ ├── Google_[Chrome]_Default.txt
│ └── Microsoft_[Edge]_Default.txt
This is where things get interesting. Your browser has likely asked you if you would like to store information which was entered into an online form. This could include your name, address, email, or other unique detail which gets entered into websites often. If you allow your browser to store this data, stealer logs easily collect it into their systems. Below is partial (redacted) data extracted from a victim.
Name: email
Value: [email protected]
===============
Name: username
Value: skxxxx22
===============
Name: lastname
Value: Loxxx
===============
Name: first-name-field
Value: Alixxx
===============
Name: address
Value: 20xx xxxx Lane
===============
Name: city
Value: Moxxx
===============
Name: phone
Value: 209-xxx-xxx
===============
Name: dob
Value: 10/xx/20xx
===============
Name: VIN
Value: kmhtcxxxxxxxxx
===============
Name: keyword
Value: 20xx Subaru xxxx
===============
Name: card-name
Value: Alixxx Loxxx
===============
Name: expiration-date
Value: 0x/2x
===============
I now have the name, DOB, home address, email, cell, vehicle, and partial credit card details of the victim.
├── Cookies
│ ├── Google_[Chrome]_Default Network.txt
│ └──Microsoft_[Edge]_Default Network.txt
Your browser stores temporary internet files about your credentialed sessions. I may not have your password to your email account, but possessing the cookies from your browser could allow me to steal your credentialed session and replicate access to your account. The following details could be beneficial to a criminal (obviously redacted and abbreviated).
.paypal.com TRUE / FALSE 196941xxx cookie_check yes
.paypal.com TRUE / FALSE 168533xxx cookie_prefs P%3D1%2CF%3D1%2Ctype%3Dimplicit
.paypal.com TRUE / FALSE 196941xxx d_id 9ebfcxxxe8545ae9a39xxx2d228xxx116537xxx
.paypal.com TRUE / FALSE 1969xxxG8 KN2xxx0aJZzhbL_R4HkiO_kHmbxxx76b5_yMTkUPrF-Ml6xxx
.paypal.com TRUE / FALSE 1685334379 X-PP-ADxxxYsNaAuNxxxHBuQ9dI
.paypal.com TRUE / FALSE 1716870381 _ga GA1.2.137xxx.165379xxx
.paypal.com TRUE / FALSE 1716912230 login_email lopxxxgmail.com
.paypal.com TRUE / FALSE 1969417578 rmuc KhGxxxmVv_x1Oo9gQ7axxxUk
├── DomainDetects.txt
This file offers immediate access to the priority domains which exist in the overall record. This allows criminals to quickly identify logs of interest.
PDD: [Amazon] amazon.com (2), [Games] steamcommunity.com (2)
CDD: [PayPal] paypal.com (40), [Amazon] amazon.com (14), [Games] battle.net (11), [Games] epicgames.com (1), [Games] steamcommunity.com (8)
├── ImportantAutofills.txt
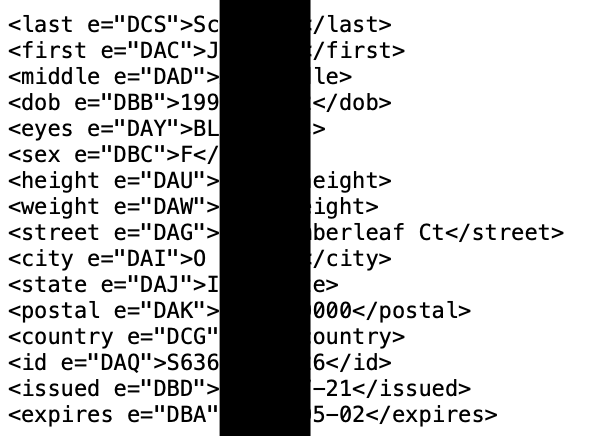
This file parses data from the stored form fields which will be most beneficial to a criminal. The last two lines of my example suspect appear as follows. I also see full credit card details presented here often.
dob: 06/xx/xx
ssn: 248xx2xxx
├── InstalledBrowsers.txt
This file identifies all installed browsers and versions.
1) Name: Google Chrome, Path: C:\Program Files (x86)\Google\Chrome\Application\chrome.exe, Version: 102.0.5005.115
2) Name: Internet Explorer, Path: C:\Program Files\Internet Explorer\iexplore.exe, Version: 11.00.22000.1 (WinBuild.160101.0800)
3) Name: Microsoft Edge, Path: C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe, Version: 102.0.1245.44
├── InstalledSoftware.txt
This file presents all applications installed within the machine. While this may not be extremely valuable to a criminal, it is gold to an investigator. If my target possesses a stealer program, I get to monitor a lot of details about the person's computer usage. In the following example, I would know which VPN my target uses, hardware details, and preferred games. That could lead to quite a social engineering attack.
1) Adobe Acrobat Reader DC [22.001.20117]
2) Adobe Creative Cloud [5.5.0.617]
3) Adobe Genuine Service [7.7.0.35]
4) Adobe Photoshop 2021 [22.1.1.138]
5) Adobe Refresh Manager [1.8.0]
6) Epic Games Launcher [1.1.279.0]
7) ExpressVPN [7.7.12.4]
8) ExpressVPN [7.7.12.4]
9) Google Chrome [102.0.5005.115]
10) HP Audio Switch [1.0.179.0]
11) HP Connection Optimizer [2.0.17.0]
12) HP PC Hardware Diagnostics UEFI [7.6.2.0]
13) Intel(R) Chipset Device Software [10.1.18295.8201]
14) Launcher Prerequisites (x64) [1.0.0.0]
15) LOOT version 0.16.0 [0.16.0]
16) McAfee LiveSafe [16.0 R27]
38) Minecraft Launcher [1.0.0.0]
39) NVIDIA Texture Tools Exporter for Adobe Photoshop [2020.1.3]
40) Razer Synapse [3.7.0531.052416]
41) Red Dead Redemption 2 [1.0.1436.31]
42) Rockstar Games Launcher [1.0.59.842]
43) Rockstar Games Social Club [2.1.3.7]
44) Steam [2.10.91.91]
45) UE4 Prerequisites (x64) [1.0.14.0]
├── Passwords.txt
This file presents all of the passwords stored within all browsers. This is why it is so important to only use reputable password managers, and never the native browser password storage option. Below is one of 56 examples for this victim, redacted. The original file displays all passwords in full.
===============
URL: https://www.amazon.com/ap/signin
Username: xxxxxxx
Password: xxxxxxx
Application: Google_[Chrome]_Default
===============
├── Screenshot.jpg
This is one of the most interesting pieces. It is a screen capture of the victim's machine at the time of infection. The following actual example (slightly redacted) identifies the person's video interests, TikTok favorites, toolbar shortcuts, Google avatar (redacted), and an overall state of the computer at the time. This is quite invasive and can be a great lead in the investigation.
└── UserInformation.txt
The last file displays general details about the system, including the victim's IP address, hardware, location, and date. An example is below.
Build ID: REDLINEVIP
IP: 192.xx.xx.xx
FileLocation: C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe
UserName: xxx
Country: US
Zip Code: xxx
Location: xxx, Texas
HWID: 72xxxxxxxxxxxxxxxCAF6
Current Language: English (United States)
ScreenSize: {Width=1920, Height=1080}
TimeZone: (UTC-07:00) Mountain Time (US & Canada)
Operation System: Windows 10 Home x64
UAC: AllowAll
Process Elevation: False
Log date: 19.06.2022 8:49:35
Name: Intel(R) Core(TM) i7-10750H CPU @ 2.60GHz, 6 Cores
Name: NVIDIA GeForce RTX 2060, 4293918720 bytes
Name: Total of RAM, 12126.75 MB or 12715814912 bytes
Putting it all together:
You may be wondering why I get so excited about these logs when they expose sensitive details about innocent victims. I have two main reasons.
First, it helps us defend our clients. We have had over a dozen clients who unknowingly installed a stealer virus. Our systems caught the infection within a few days and allowed us to contact the client to make notification. We have helped numerous organizations which had unknown infections within their network. Some of our staff calls this our "Pre-Crime Unit".
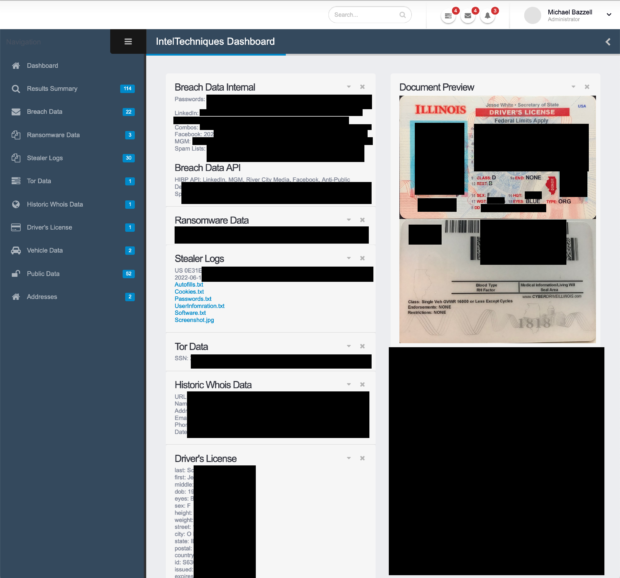
Next, it could be a priceless investigation tool. I have had numerous suspects within my own investigations who were victims of stealer logs. When this happens, I can see all of their emails, usernames, and passwords. This has uncovered alias names and other deceitful tactics used by the suspect. If my target is the victim of stealer logs, my entire investigation is about to be wrapped up quickly. If I have the HWID, I can search through our troves of logger data to identify even more vital info about the suspect.
Because of this, we aggressively collect stealer log data every day. Some days we ingest over 250GB of this data.
Tomorrow, I offer a glimpse into the ways in which we use this data within our internal investigations portal.