I have been due for a new laptop for some time. Mine both work, but they have been beaten up by constant travel and I am due for a performance boost. I am also growing tired of having a machine for personal work and a dedicated OSINT/Breach machine. I have been watching the System76 site for a while and monitoring their new products. I finally executed and now have a single System76 Darter Pro with truly secure, fully encrypted, dual-boot internal drives ready for all of my needs. It feels like the right time to update my preferences for a Linux laptop, and explain how I choose the ideal machine.
First, we need to define the scope of the ideal laptop. If you are a macOS user, then you just find the shiny product you like and customize the specs. If you are a Linux user, you may feel overwhelmed by the options available from many providers. If you are a Windows user, please consider becoming a Linux user.
You could take practically any used Windows (or Intel macOS) computer and reformat the drive with Linux. That is a great way to get a feel for the operating system before committing. If you know you want to switch to Linux, then I recommend purchasing a new laptop designed for Linux. There are a few providers who cater to this, and I hope to eliminate a couple right away. Purism makes an outdated and overpriced Linux laptop, but I would never consider buying anything from them. They are still trying to fulfill orders from five years ago, and refuse to provide a refund if they never ship your product. I am shocked they are still in business, please avoid them. Framework came out with a very interesting product which has swap-able parts, such as Ethernet or USB ports, but I do not recommend them either. I have witnessed numerous devices fail and the components wear out way too quickly. Finally, Tuxedo offers dedicated Linux machines, but they cater mostly to European customers. I have no issues with Tuxedo computers, but I believe we have a much better option.
It should be no surprise to readers that I am a System76 fanboy. I have been recommending their products for many years, and I use them daily. It is not because they are making a physical product which is unavailable anywhere else, because that is not true. System76 uses mostly Clevo machines purchased in bulk which anyone can buy. The reason I choose System76 is their custom open-source firmware and attempts to disable as much of Intel's processor management as possible. These two options cannot be overstated, as well as their customer support.
When you purchase a System76 laptop, they have already eliminated the stock firmware and replaced it with their own customization of open-source coreboot. This removes all of the unknown blobs, connections, and suspicious software which is always running at the root of your machine, regardless of encryption. I see so many people screaming about the importance of full-disk encryption, but most of them are running closed-source firmware outside of that encryption which could be doing malicious things. Therefore, I only consider System76 machines for my personal Linux usage.
This presents the next issue. There is some substantial complexity of choice when buying a System76 laptop. This has gotten better since they eliminated a couple of older models, but today you still must choose from the Lemur Pro, Darter Pro, Pangolin, Adder WS, Oryx Pro, Serval WS and Bonobo WS. This is a very personal choice, but I offer my process of elimination.
First, I do not need dedicated graphics. I am not a gamer and I do not process 4K video all day. I do not mine cryptocurrency and I simply do not want to pay a premium for power I will never use. This eliminates the Adder WS, Oryx Pro, Serval WS and Bonobo WS for me. We are left with the Lemur Pro, Darter Pro, and Pangolin. The Pangolin is out for me because it has an AMD processor, which possesses its own processor management operating system which cannot be disabled. Both the Lemur Pro and Darter Pro have most of Intel's Management Engine (ME) disabled by default, so either works for me.
I insist on both USB-A and USB-C ports, and both machines offer that. I prefer to possess a microSD slot, and both have me covered there too. I also insist on an Ethernet port. I often need to connect directly to a firewall or network without Wi-Fi, and this is essential to have. Only the Darter Pro has every port I need with all of the features I demand. I am writing this post on my new Darter Pro.
I prefer a 14" model since I travel often. I am sure the 16" has a beautiful screen, but the mobility is more vital to me. The machine works great and looks slick. If you are transitioning from any other Windows computer, I think the overall build and feel will be superior to your previous experiences. If you are a macOS user accustomed to the latest MacBook Pro machines, many previous Linux devices may feel "plasticy" or "cheap". This one does not. The new Darter Pro seems to have the most premium build of the lightweight models. I have been testing various Linux laptops for many years, and this one is hands-down the best I have had. Some will say it can never compete with the aesthetics of a MacBook Pro, Air, etc., but I think it comes close. That leads us to the specs.
The new Darter Pro offers the new Intel 4.5 GHz Core Ultra (U) 5 or the Intel 4.8 GHz Core Ultra (U) 7. I went with the 5 at a $129 lower price. It has plenty of speed for my usage. If you know you will need the extra boost, then go with the 7. You cannot change the processor after purchase (but you can modify the RAM and drive). I have yet to max out the processor, so I have no need for the upgrade.
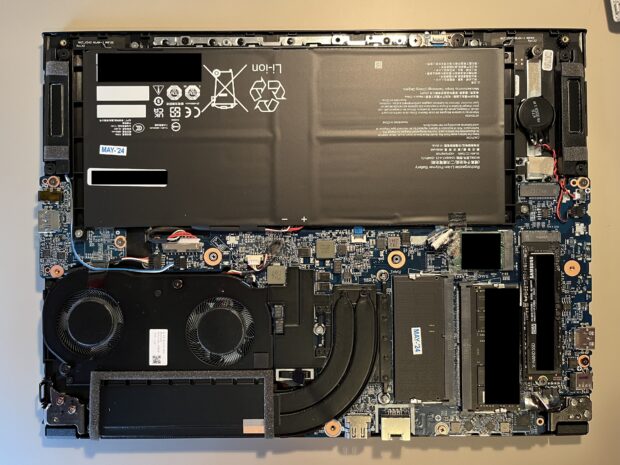
I went with 32 GB of RAM, which I think is overkill for most people. Since I use multiple virtual machines simultaneously, I wanted to be covered. Again, I have yet to come close to maximizing the RAM usage, but 16GB could have caused me some issues.
I have a 4 TB internal PCIe4 M.2 NVMe drive. That is also overkill for most, but I will be using this for breach data work which can quickly exceed a couple of terabytes. Having this large internal SSD allows me lightning fast queries and imports. Shaving off a few seconds here or there may seem like a small benefit, but it becomes vital when dealing with terabytes of data.
The screen has a matte finish and looks great. I am mostly at my home office connected to an external monitor, so this is not a priority to me anyway. However, I spent a few hours on the unit itself and found no issues with the 14" screen. The brightest setting was actually too bright. The keyboard is great, and better than the previous generations. There is much less of a "hollow" feel which is common in Linux machines. The track-pad is also better than the previous models, and has a nice matte "velvet" feel to it. It is extremely responsive, especially when tapping to click. The embedded Intel graphics are all I need, and allowed me a longer battery life. I never felt the need for a dedicated graphics card.
Battery life is never the same for everyone. Light browsing may provide a long range while heavy processing might reveal minimal life before recharging. Since I am usually plugged in, battery life is not a priority for me. However, I achieved almost 5 hours while thoroughly testing for this review.
One thing I did not expect to make a difference was the placement of the Ethernet port. This model has it on the back of the device instead of the side. I like this feature. It keeps the cable out of my site and away from my external mouse. HDMI is also on the back. I do not use Bluetooth, but the Wi-Fi 6E performed as expected. Internal transfers approached the speed limitations.
As I recommend for others in my Extreme Privacy: Linux Devices book, I rely on Pop!_OS as my operating system. I no longer use Ubuntu on any machine or VM, and Pop!_OS has spoiled me with their application storefront and overall fluid environment. I am impatiently awaiting their new Cosmic 24.04 release, which is a full rebuild of the OS. Until then, the current stable build works great on this machine.
Overall, the machine just "feels" good. It feels more solid, possibly more "premium", than previous models. The size is perfect for me and the value is appropriate. My machine has a retail price of $1,697.00, but I chose a 4TB internal drive. The same machine with 1TB drive would have been $1,393.00 ($100 less if pre-ordered). That is a great deal for a dedicated Linux machine with open-source firmware and disabled Intel ME. I know of no other device which gives you this. Combine this with a full-disk encrypted Pop!_OS and you have what I believe is the most private and secure system available today. It is both my daily driver and my breach data machine (more on that soon).
Below are some photos I took to provide some insight which may not be obvious in the stock images on the System76 website. This is a comparison to the 14" MacBook Pro.

MacBook Pro (left) and Darter Pro (right)

Darter Pro (left) and MacBook Pro (right)

MacBook Pro (top) and Darter Pro (bottom)

MacBook Pro (top) and Darter Pro (bottom)

MacBook Pro (top) and Darter Pro (bottom)
In the next post, I will explain how I use multiple internal NVMe drives to securely dual-boot full-disk encrypted operating systems within open-source coreboot for true security. This allows me to safely carry one machine for both personal and breach data usage. Readers of my book Extreme Privacy: Linux Devices will also receive this content within their book updates by June 1, 2024.
Disclosures: I was not paid to write this article and I was not asked to write this review. I gave no editorial control for this and the opinions are mine. System76 allowed me temporary access to a demo unit before it was publicly available. I am not a System76 affiliate and I do not receive any payments for orders placed due to this review. I just like the machine.