I like to check my credit reports annually to make sure that no unauthorized accounts have been opened in my name. While I prepare for a podcast episode about the content of various credit reports and consumer data profiles, I went to annualcreditreport.com to pull my report from the three major credit bureaus. For the first time, I received the following general error declining my reports.

While I have previously had problems confirming my identity with two of the three credit bureaus, I have never been blocked from the entire annualcreditreport.com website. I proceeded to manually request the reports from each bureau within the site, but received resistance from each, as follows.
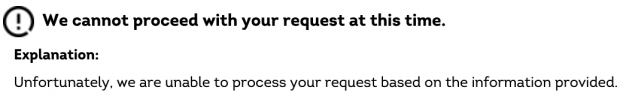


I consider this a "win". The only single aggregated website for requesting free credit reports can no longer confirm I exist. If I can't access them, neither can a malicious adversary. However, this presents a problem. How do I check my reports? I can still submit a request via postal mail at the following link, but that can take 30 days.
https://www.annualcreditreport.com/manualRequestForm.action
Fortunately, I have already "Planted My Flag" with all three bureaus which provided direct login credentials to each service's website. Equifax and Experian allowed me immediate access to my reports, but TransUnion is still unable to confirm my identity, with the following error.

I have submitted this final request via postal mail. Hopefully it arrives in time for the show. My plan is to provide a summary of the data which various credit and data broker services possess about me after five years of Extreme Privacy. I also want to provide warnings about the restrictions applied when we go to the extreme and the lessons I have learned from my mistakes. I will announce everything soon on the podcast. My CLEAR and LexisNexis reports were a bit surprising.