Last week, an unknown "hacker" released a copy of a user database from the IronMarch forum, which was an online neo-nazi meeting place until it was shut down. An archive of the public site can be found at https://web.archive.org/web/20170509142136/http://ironmarch.org/. The dumped data includes a full copy of all content, including details such as emails, IP addresses, usernames, and private messages. I decided to dig into it a bit and see what could be gleaned. The original leak has been removed from Pastebin, but several clones appear daily. The following is a redacted version of a few entries.
Four Suited Jack:[email protected]:e0e501f3e4e49d6c67378d9d06763298:?ET\"e
Jamie M:[email protected]:8ecdc4d6401055df380ab007c0c31b5b:t32hj
Ritz:[email protected]:159e7b09066e91fcb15008943d114b6e:vy:I0
This represents the username:email:encrypted password of each user on the forum. My first task was to parse out all of the email addresses. I saved the original leak file as Ironmarch.full.txt and executed the following command in Linux.
grep -E -o "\b[a-zA-Z0-9.-]+@[a-zA-Z0-9.-]+\.[a-zA-Z0-9.-]+\b" < Ironmarch.full.txt > Ironmarch.emails.txt
This presented a clean file containing only the email addresses of every user. I then connected to a covert Gmail account, accessed the Contacts, and exported the only contact in this account to a CSV file. This provided the template desired by Google for import. I copied and pasted the entire list of email addresses within this template and gave each of them a unique last name of 1,2,3,etc. This presented a CSV file ready for import. The following is a partial view.
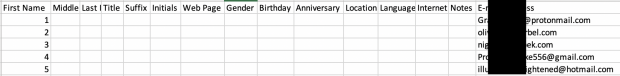
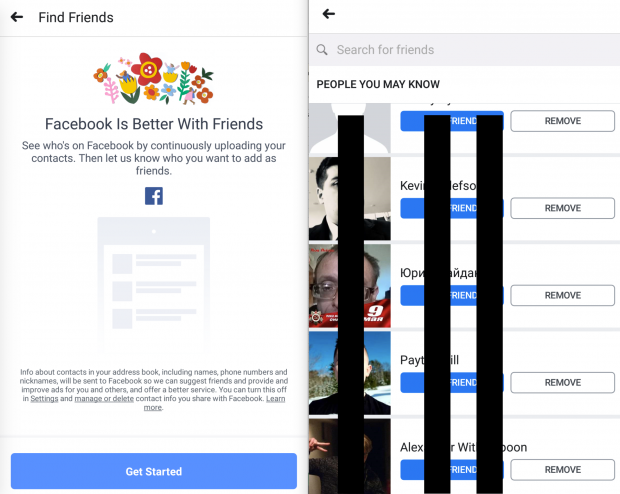
I imported this CSV into my Google Contacts which now tells Google these are my "Friends". I then launched a new Android virtual machine through Genymotion and connected to the covert Google account. This virtual mobile device now associates all of these email addresses with my own address book. I connected to the Facebook app, asked it to "Find Friends, and was immediately presented with numerous Facebook accounts which were associated with the email addresses of the Ironmarch members. Below is an example.
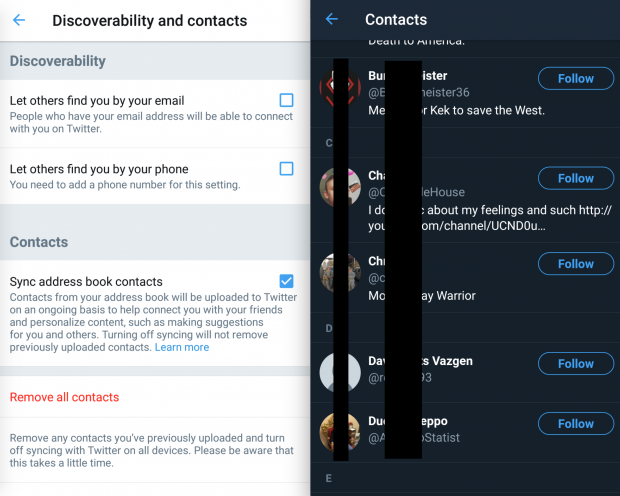
I then repeated this process with Twitter:
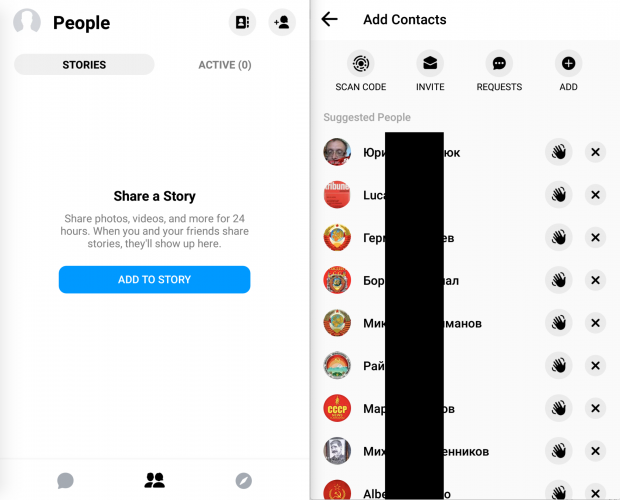
and Instagram:
OSINT Lessons Learned:
Breaches and leaks of online forums are very common. Lists of email addresses may identify interesting information about the types of members. However, identifying social network accounts of members of hate groups can be much more revealing. I quickly located numerous personal accounts registered in real names, all from the connection to an email address.
PRIVACY Lessons Learned:
I also identified many accounts which were likely used during covert investigations. When I submitted the email addresses as contacts through a foreign dating network, I observed an account connected to a police cyber-crimes investigator. This is probably due to him using a real address when registering for an account on the forum. This is sloppy, but I have been guilty of this myself many years ago. If you are tasked with investigating online hate groups, or anything else really, be sure to always use a unique email address and password, which will never be used anywhere else. Social networks and other online communities make it very easy to connect accounts with real people.