Note: This post is a supplement to the podcast episode with the same title located at https://soundcloud.com/user-98066669/226-personal-ransomware-exposure.
When we think about ransomware victims, I suspect most of us think about companies having their data encrypted and being extorted for Bitcoin payments in order to obtain the decryption tool which will unlock their documents. With more companies possessing proper backups due to the awareness of this criminal activity, we are now seeing ransomware groups focus more on exposure of data instead of decryption. This presents a new problem for all of us. It is now OUR data which is often exposed to the world when companies refuse to pay the ransom.
To be clear, I never support or encourage ransomware payments. However, I do support resistance when companies and government institutions demand our information and then store it insecurely. On my show, I talk a lot about my methods to sanitize my personal information when requested because I know it is likely to appear online due to poor privacy policies or accidental exposure. Let's take a look at some recent ransomware data dumps which are now publicly available and may be leaking YOUR personal details.
Accountants often demand to store copies of IDs and tax forms on your behalf. My account/attorney rolls his eyes when I insist on storage within encrypted containers and transmission only via encrypted email. I believe this is all justified. Clients of a California law firm now have all of their data exposed within a ransomware dump made public last week by a group called "Clop".

This includes tax forms displaying names, DOBs, and SSN, as seen below.
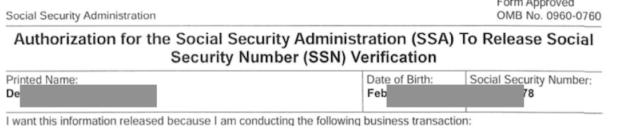
This is the main reason I insist that my attorney either store data within a secure encrypted container or allow me to be responsible for storage of my own docs.
Employers demand tax forms from us to legally pay us, but then store them with the same security as the rest of their daily documents. The following is one of many employee tax forms collected by a nutritional foods company which was hit with ransomware this year by a group called "Clop" which is now publicly available.

This is one of the many reasons I conduct all business in the name of an LLC and only provide EINs issued by the IRS for all transactions.
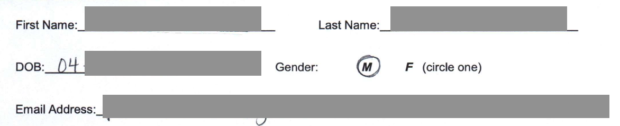
Universities and colleges demand our personal details and then include them within documents stored insecurely. The following Miami university breached document publicly discloses full name, address, DOB, ethnicity, phone, cell, email, and relatives. I suspect people search websites will soon start including ransomware dumps within their infrastructure.
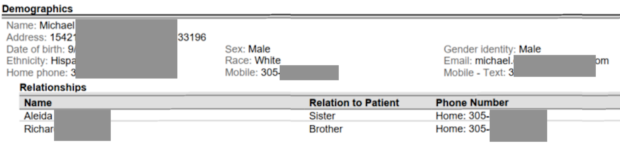
A Colorado school went further by releasing class schedules and grades after they were hit with ransomware.
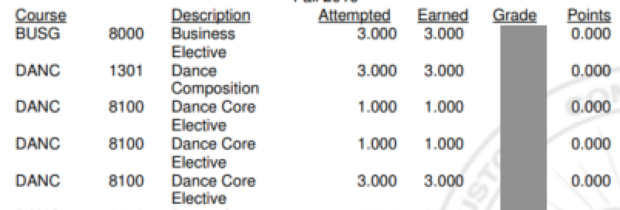
Digging into the files further identifies every student's overall GPA which allows the public to now monitor his progress as a student.
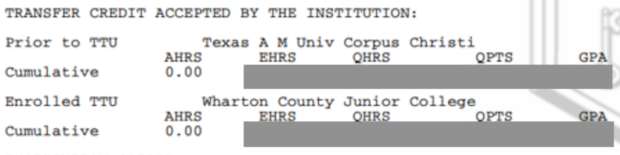
I have no secure options for this problem. We have no control over school storage of our data.
All of the forms your doctor or dentist makes you sign are rarely securely stored. The following redacted partial form was released after a dentist office refused to pay a ransom to a group called "Conti" and terabytes of data were exposed online.
This is the reason I always resist signing unnecessary paperwork and scrutinize HIPAA release forms. We cannot refuse everything, but we can minimize our exposure.
The apartment or home you have leased includes numerous contracts. When the property management company, in this case a business in Canada, gets hit with ransomware and ignores the extortion demands, all documents get released publicly.
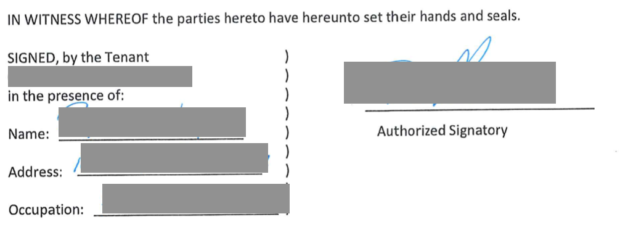
This is one of many reasons I title any home ownership or lease within the name of a trust or LLC.
Physicians, surgeons, and dentists often capture digital photographs of various conditions. A hospital suffered a ransomware breach by a group called "Vice Society" and did not pay the criminals. As a result, all of their stolen data was published to the internet, including images of their patients' illnesses, including the following redacted image.

This is one reason I SOMETIMES ask doctors to either avoid unnecessary images or delete them after any procedure is complete.
If the images present within the data dump were not enough, a Word file titled "Login and Passwords" is included for access to third party services. I may or may not have confirmed that all of the passwords still work. This is why I never recommend storing passwords locally in an unprotected document, and only recommend locally-stored secure password managers with encrypted data.
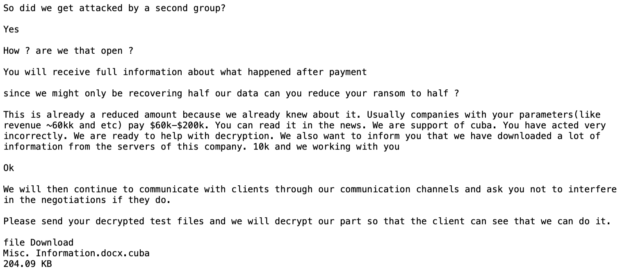
Since my company often assists clients with ransomware attacks, I find the chat logs between businesses and the criminals especially valuable. Many of these logs are stored within the victim computers and become part of the data dump through the offender's website. The following is a partial display of a chat between a dermatologist office and the criminals who attacked their network. These can be a great source of education before engaging with ransomware criminals.
Many ransomware data leaks contain full Outlook PST files which include every incoming and outgoing email associated with a specific email address. The following is a partial list of these files, each several gigabytes in size, downloaded from a ransomware publication after a city refused to pay the extortion. The content of these files is incredibly sensitive.

This is why I consider every email I send to be public information. I never send anything I would worry about becoming publicly available. I reserve sensitive conversations for E2EE ephemeral messaging.
The next time a business demands your personal data or a copy of your ID, consider this post. When they ignore your resistance to provide personal details which are not required for the business being conducted, explain your concern through these examples. When your friends and family call you paranoid or difficult for wanting to keep your information private, know that you are not alone. If you would like much more information about the ways I protect the privacy and security of my clients, please check out my book Extreme Privacy.
