WARNING: The following post explains my actions taken on behalf of a client while possessing full written consent to access these accounts. Taking any action to access someone's account without consent is illegal. Never replicate these steps on any accounts which you do not own. The redacted screen captures are shared here with consent of the client with hopes that they help others avoid becoming a victim of this type of attack.
Recently, a client conducted a full privacy reboot including a new home titled to an anonymous entity. This client had read the books and had already established most of the digital strategies. While within a transition from his old life to his new anonymous life, he went on vacation and asked us to dig in deep. He wanted to know anywhere he may still be vulnerable before he gets to his anonymous home. With written consent to access anything attached to him, we attacked. We share the results with encouragement from the client to spread awareness.
I started with breach data, as it is always the most fruitful. I confirmed that all of his exposed passwords had already been changed and I could not access any of his breached accounts. However, I noticed something interesting. In a very recent data breach, a telephone number which I had not seen during his initial assessment was associated to one of his newer email accounts. This breach was associated with an online vendor which he had used to purchase an item. The address was his PMB and his password was properly hashed and salted. However, the new number was a big lead.
I searched this number through various caller ID services and confirmed it had been ported often. This immediately made me suspect it was associated with a temporary number service or VoIP provider. A buried Google search finally gave me the answer. It was a number associated with OnlineSIM, a free SMS text receiving service available to the public.
These services allow you to use temporary burner numbers to receive SMS messages without giving out a true cellular number. I don't like them. While I have promoted the idea for temporary email addresses when you need to bypass a websites signup requirement in order to access content, I never recommend this for telephone numbers. You will understand the reasons why soon.
I went to OnlineSIM, but did not see this number as an active option. I had to select the "Archive Numbers" option and then choose the target's country. This displayed previous numbers used by people visiting the site along with an archive of the incoming messages. The image below shows a live unredacted view of a random U.S. number which displays archived incoming SMS text messages to access Apple, Cupcake, and PingMe accounts. The Online Numbers area is full of active numbers which could be abused in real time.
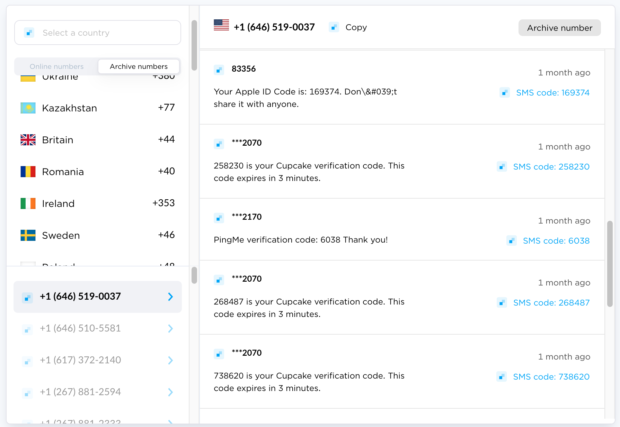
I suspected that my client had created an online order, the service demanded a valid number, and he provided a burner number from this service in order to bypass the requirement. This company had already been breached, so I had all of the data from the order (which was not too concerning). I wanted to know anywhere else he had used that number.
The archive of messages at OnlineSIM for that number included content generated by many different people. These numbers and messages are public and anyone can abuse them as needed. In order to stay legal, I wanted to make sure that I only accessed accounts owned by my client. I reassessed the breach data from his online purchase and identified the exact date and time of the order. I looked through the archives until I found the verification text from the product he ordered at that same date and time. This occurred within the past month, so identification was easy. I then analyzed the SMS messages which also occurred with that temporary number around that time.
I am cheating here a bit because I know my client. I know that he was in the process of relocating around this time and was likely using this burner number to create new "anonymous" accounts for various services. I was most interested in the following message, received a few minutes after the text which I had already confirmed for my client.

This is verification code used to log into an AirBNB account. Again, I cheated. I asked my client if he had used this number to create a new AirBNB account and he confirmed he had. I did this to stay legal, but a bad actor would have simply tried to login with the number. I went to AirBNB and chose the option to log in:
I then entered the publicly-available number from OnlineSIM, and received the confirmation screen:
Since this temporary number was "archived", I could not receive any new messages through the public site. However, one could "rent" that number through this service for a few bucks. This would allow anyone to receive the confirmation text and access the account:

One could then access all messages:
And access his current location:
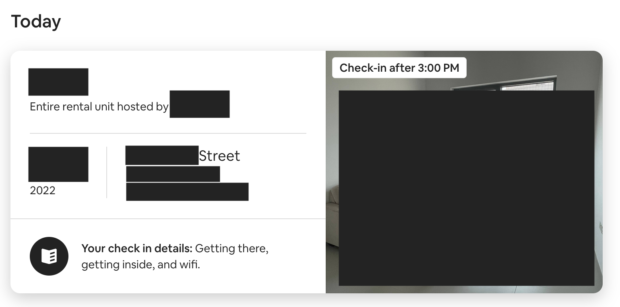
With unrestricted access to this number, one could log into his Instagram using number verification, which would give access to the settings of his account:
This would provide a new email address and secondary number to begin searching. Anyone with malicious intent could pluck away at the live incoming SMS text messages on OnlineSIM and take over most accounts. While writing this, someone just used this service to create an account on Signal. I could use the same number to take over their account (I did not).
I stopped there because I was worried I would eventually access someone else's content without authorization. As I write this, the following messages were displayed in real time, which confirmed various accounts associated with a public UK number. Anyone could hijack these accounts by requesting account access or a password reset via SMS confirmation.
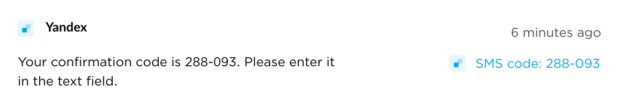


The damage for my client was done. If I were an adversary, I would have been able to use breach data to identify a burner number used for an account, check the archives of that number's use, access any accounts which now use that number for verification, and determine where he was sleeping under an alias name through AirBNB. I played by the rules with written consent. A criminal would not care about that. THIS is why I never recommend temporary burner telephone numbers for anything "real" or for accounts which allow login (or password reset) via text message verification.
I mentioned temporary email "burners" have a purpose, but we must be careful not to exceed their scope. I only use these services, such as Mailinator, for the following scenarios.
- A website requires a valid email address to send free content (PDF)
- A website requires a newsletter subscription to access content
- A website requires an email verification to access content.
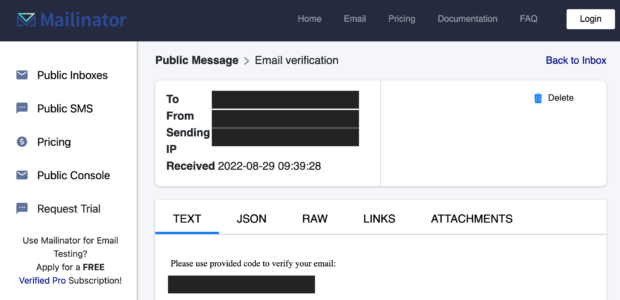
Anything else is off limits. Last week, I identified a Mailinator email address associated with a client within breach data. With consent, that allowed me to access that mailbox:
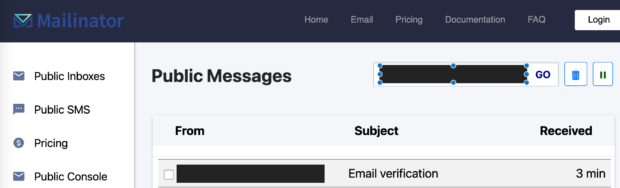
I could then access numerous accounts by resetting her password to each service and receive the result in this public mailbox:
Burners have their place, but we must be careful how we use them. Finally, we must also never use emails which we do not own. We have all been on a site which requires an email to see content, so we enter "[email protected]" just to get past the screen. Worse, we may create an online account with a similar address since a lot of services do not verify ownership of the address (Reddit, Mozilla, etc). I like to register commonly-used addresses just to see what comes in.
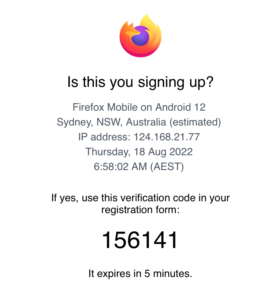
As an example, I registered an email address similar to [email protected] (not the actual address). Every day, I get emails welcoming me to a new service or asking me to confirm my address after people use it as a bypass. Someone recently used this email to create a Mozilla account:
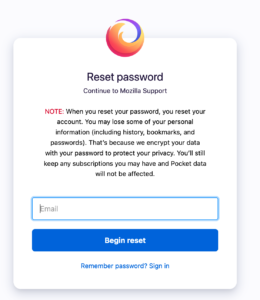
Sometimes, I can't resist and I change the password:
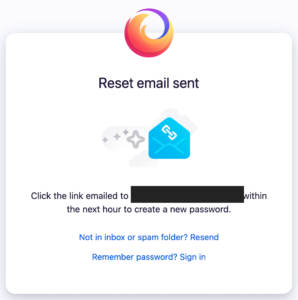
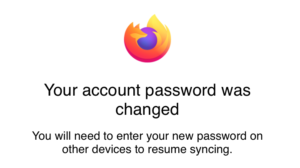
I then had access to their Firefox Sync, Pocket, Add-Ons, and Monitor data. This is not a huge invasion, but it could be much worse. Last month, someone attached my generic-sounding email account to their bank because they demanded a secondary email address. I now get copies of their emails and could reset their password:
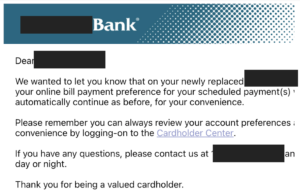
Please don't do this.


















