I own hundreds of VOIP telephone numbers throughout every state's area codes which all forward to a single email inbox. The benefit of this is the immediate availability of different numbers for various purposes. The annoyance of this is the increasing number of SMS phishing attacks. On Friday, I received the following SMS message to five numbers which possess Illinois area codes.
"Illinois Department of Transportation (IDOT) Driver License Waiver Validation. Validate your details at https://forms.gle/EmxTZFNY8z7paZNb9"
This Google Forms address translated to the following URL:
https://docs.google.com/forms/d/e/1FAIpQLSfIQb0LIuvdtIodJnJiHiffnwgwNh8moq7qHioEouJEHZ9fPA/viewform
Screen captures are below:
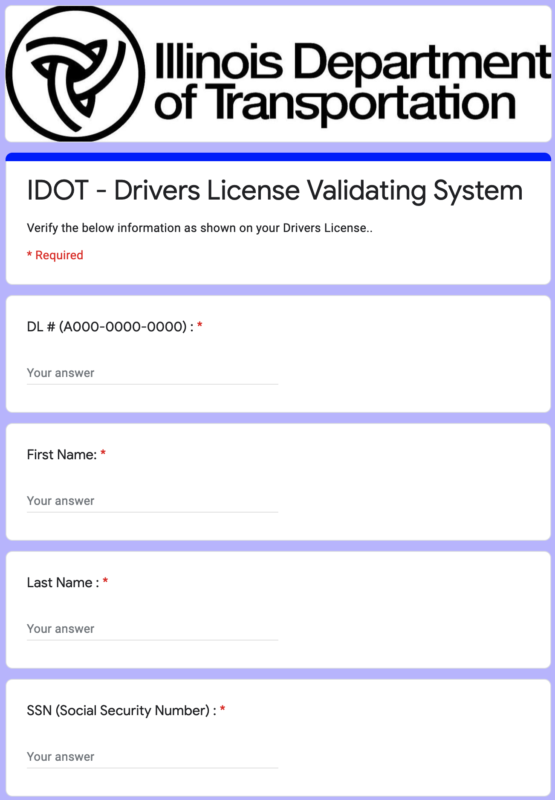
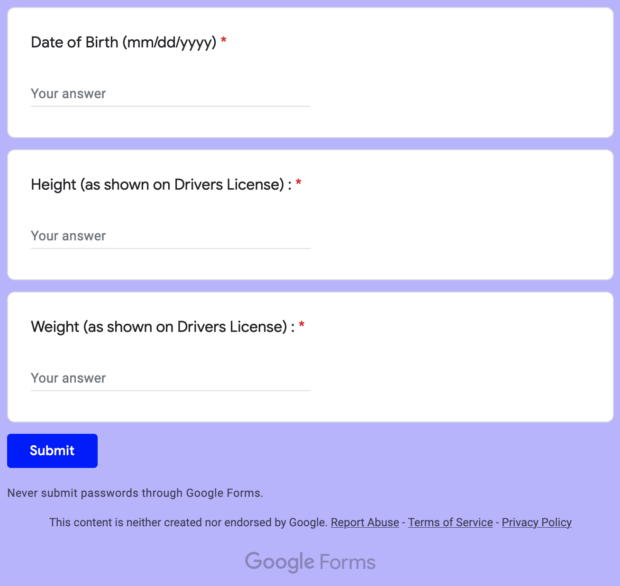
This is obviously a phishing attack to steal people's identities, but let's dig in deeper. These messages arrived in chronological order to the numbers. My numbers have a structure similar to the following:
6185551212
6185551213
6185551214
6185551215
6185552000
The messages to the first four arrived within seconds of each other and the fifth number received the message about three minutes from the first. This makes me believe that the messages are being sent to blocks of telephone numbers regardless of whether they exist.
Using OSINT tools, I was able to identify the Gmail address associated with the Forms account. This account appeared within several breaches. A query of these breaches displayed the name and home address of the account owner, who is likely not involved in this scam. The passwords to all of the breaches associated with her email account were identical. The offender probably used her recycled password to access her Google account and generate the Google Form. I have attempted to contact her at a secondary email account, but have yet to receive a response.
The phone number sending the messages (5809542353) is a Verizon prepaid account, but may have been spoofed. I am intentionally leaving the number and URL within this post in case anyone receives these messages and conducts a search for details.
An hour later, I received a similar message to all of my Texas and California numbers. These all included custom forms for the Texas and California departments of motor vehicles.
I made several attempts to report all malicious forms to Google, but I do not expect to any response. As of today (Sunday), the links are still active. I currently have a script entering false details into these forms multiple times every minute until Google picks up the activity and removes the content. I realize I am preaching to the choir here, but please help spread the word to those less tech-aware.


