I have always maintained an Email Search Tool as part of my set of online investigation tools at https://inteltechniques.com/menu.html. This month, a series of reports about a huge new set of data breaches emerged and created unnecessary panic. While there truly was a new public database released containing hundreds of millions of email addresses and passwords, the vast majority was old data which had surfaced several years prior. Regardless, it was a good reminder that we should be diligent about checking our own email accounts against the various online repositories that possess most of the public leaks/breaches/data dumps being abused by amateur criminals. Investigators should also take advantage of this information as part of every email investigation. Recently, I made several changes to the Email Search Tool as seen below.
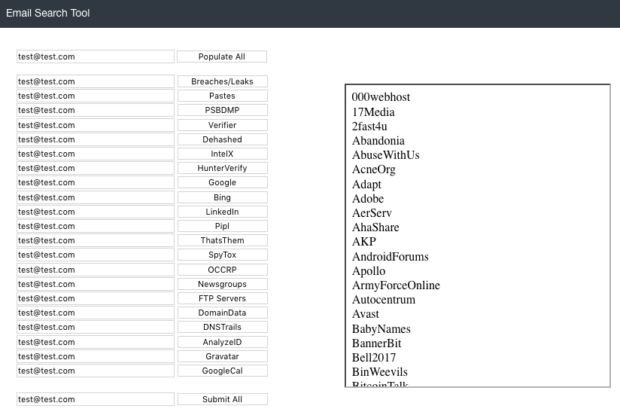
In this example, I entered a test email address and chose the "Populate All" option. The following details explain the first six options, which are the most lucrative.
Breaches/Leaks: This tool queries the HIBP API and presents the results in the window to the right. In this example, you can see that the test email is present within numerous data breaches. The OFFENSE of this is to identify the various online accounts in use by your target. The DEFENSE is to identify your own accounts with exposed passwords and change them anywhere they have been used.
Pastes: This queries the HIBP Pastebin API and identifies email addresses that have appeared on pastebin.com, which is often used to store user credentials.
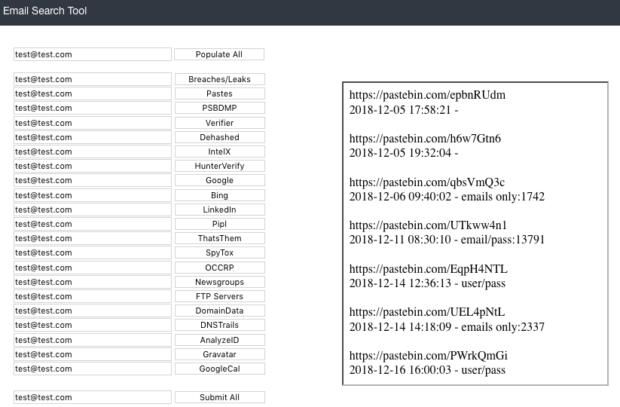
PSBDMP: This queries the PSBDMP collection of pastebin scrapes, which identifies email addresses that have appeared on pastebin.com, even if they have been removed or were never indexed by Google. The results display in the window to the right, and I have added the complete URL of each entry for further investigation. (Thanks to Justin Seitz for fixing my pathetic PHP attempt on this). This has been a huge help with my investigations. A sample entry with the dates of original capture is below.
Verifier: This opens a new tab and queries the address through the Trumail API. This identifies whether the email address is valid, has a full inbox, is a catch-all, is from a disposable email provider, and other interesting details.
Dehashed: This opens a new tab and queries the free version of dehashed.com, which displays any additional breaches that may not have been captured by the previous attempts. Paid memberships can see the password details.
IntelX: This premium option (with a free trial) also identifies pastebin posts that reference the email address. The free version will tell you that the data exists, the premium (or free trial) will display the content.
I encourage everyone to check their own email addresses on occasion. If you appear within any of these data sets, you know that an account has likely been compromised to some extent. Be sure to change those passwords to something secure, unique, and preferably randomly generated by a password manager (I use KeepassXC).